Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account

 Your new post is loading... Your new post is loading...
 Your new post is loading... Your new post is loading...
Current selected tags: 'BYOD-Security', 'English'. Clear
Worried about hackers and fraudsters gaining access to the data on your Android smartphone or tablet? You should be. But you can also reduce that risk by installing a security app on your device. Learn more: - https://gustmees.wordpress.com/2014/11/25/digital-citizenship-social-media-and-privacy/
Gust MEES's insight:
Worried about hackers and fraudsters gaining access to the data on your Android smartphone or tablet? You should be. But you can also reduce that risk by installing a security app on your device. Learn more: - https://gustmees.wordpress.com/2014/11/25/digital-citizenship-social-media-and-privacy/
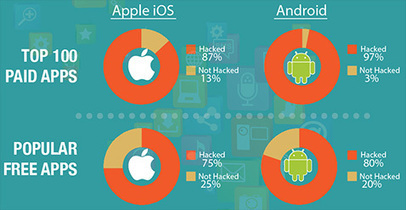
97% of the top 100 paid Android apps and 87% of the top 100 paid Apple iOS apps have been hacked, according to Arxan Technologies. Learn more:
Gust MEES's insight:
97% of the top 100 paid Android apps and 87% of the top 100 paid Apple iOS apps have been hacked, according to Arxan Technologies. Learn more: 
Gust MEES's curator insight,
November 17, 2014 8:26 AM
97% of the top 100 paid Android apps and 87% of the top 100 paid Apple iOS apps have been hacked, according to Arxan Technologies. Learn more: 
Gust MEES's curator insight,
November 17, 2014 8:28 AM
97% of the top 100 paid Android apps and 87% of the top 100 paid Apple iOS apps have been hacked, according to Arxan Technologies. Learn more:
How hackers are attacking binary code and mobile app vulnerabilities, and what you can do about it. Learn more:
Gust MEES's insight:
How hackers are attacking binary code and mobile app vulnerabilities, and what you can do about it. Learn more:
As mobile learning becomes more common, district leaders are working hard to juggle nimble adaptation in a changing environment and the desire to get it right. Learn more:
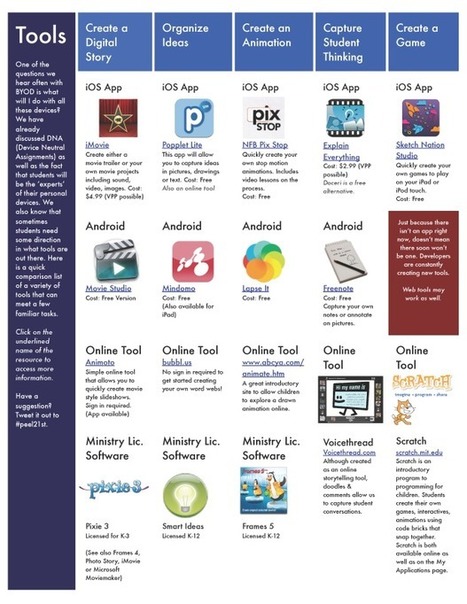
The BYOD Pros and Cons in Education Infographic highlights many of the advantages and disadvantages to letting students use personal devices in the classrooms. Learn more:
Gust MEES's insight:
The BYOD Pros and Cons in Education Infographic highlights many of the advantages and disadvantages to letting students use personal devices in the classrooms. Learn more:

Monty Bell's curator insight,
April 10, 2014 11:35 AM
A balanced discussion on a very contentious issue
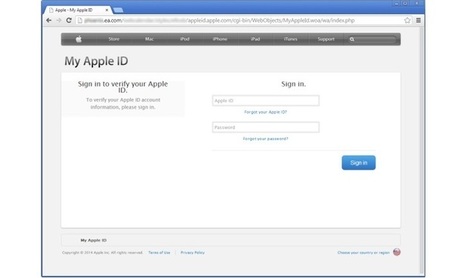
Apple phishing scams are not uncommon, but phishing pages hosted on the website of a major company are certainly worth looking at. Experts have found ... “The mere presence of old software can often provide sufficient incentive for a hacker to target one system over another, and to spend more time looking for additional vulnerabilities or trying to probe deeper into the internal network.”
Gust MEES's insight:
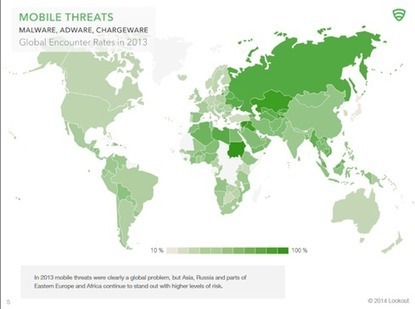
Lookout's analysis of the mobile threat landscape suggests businesses should focus on curbing risky online behavior.
Gust MEES's insight:
Distributed denial-of-service (DDOS) attack protection solutions provider Prolexic has published its Global DDOS Attack Report for the fourth quarter ...
“The prevalence of mobile devices and the widespread availability of downloadable apps that can be used for DDoS is a game changer,” explained Stuart Scholly, president of Prolexic.
Malicious actors now carry a powerful attack tool in the palm of their hands, which requires minimal skill to use. Because it is so easy for mobile device users to opt-in to DDoS attack campaigns, we expect to see a considerable increase in the use of these attack tools in 2014,” Scholly added.
I'd recommend using this chart as a jumping off point to new adventures in learning in BYOD classrooms and beyond!
Gust MEES's insight:
Learn more about BYOD:
- http://gustmees.wordpress.com/2012/07/07/bring-your-own-device-advantages-dangers-and-risks/

Dr Pam Hill's curator insight,
November 1, 2013 4:04 PM
Great ideas for BYOD PD sessions. I will be using these ideas!
Elena Evtukh's curator insight,
November 8, 2013 11:43 PM
Эффективные мобльные приложения и сетевые ресурсы для BYOD класса. В - bring (принеси) Y - your (свое) O - own (собственное) D - device (устройство) 
Melissa Marshall's curator insight,
November 11, 2013 2:24 AM
Great graphic for when you are unsure as to what your kids may have access to.
The biometrics hacking team of the Chaos Computer Club (CCC) has successfully bypassed the biometric security of Apple's TouchID using easy everyday means. A fingerprint of the phone user, photographed from a glass surface, was enough to create a fake finger that could unlock an iPhone 5s secured with TouchID.
This demonstrates – again – that fingerprint biometrics is unsuitable as access control method and should be avoided.
Gust MEES's insight:
The biometrics hacking team of the Chaos Computer Club (CCC) has successfully bypassed the biometric security of Apple's TouchID using easy everyday means. A fingerprint of the phone user, photographed from a glass surface, was enough to create a fake finger that could unlock an iPhone 5s secured with TouchID.
This demonstrates – again – that fingerprint biometrics is unsuitable as access control method and should be avoided.
Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

Gust MEES's curator insight,
September 22, 2013 4:47 PM
The biometrics hacking team of the Chaos Computer Club (CCC) has successfully bypassed the biometric security of Apple's TouchID using easy everyday means. A fingerprint of the phone user, photographed from a glass surface, was enough to create a fake finger that could unlock an iPhone 5s secured with TouchID.
This demonstrates – again – that fingerprint biometrics is unsuitable as access control method and should be avoided.
Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

Gust MEES's curator insight,
September 22, 2013 4:50 PM
The biometrics hacking team of the Chaos Computer Club (CCC) has successfully bypassed the biometric security of Apple's TouchID using easy everyday means. A fingerprint of the phone user, photographed from a glass surface, was enough to create a fake finger that could unlock an iPhone 5s secured with TouchID.
This demonstrates – again – that fingerprint biometrics is unsuitable as access control method and should be avoided.
Learn more: - http://www.scoop.it/t/securite-pc-et-internet/?tag=biometrics
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security
BYOD Security Issues: How safe is the common practice for employees to Bring their Own Device into work?
Gust MEES's insight:

malek's curator insight,
September 17, 2013 8:23 AM
A myriad of threats: * Employers often cannot assess data breach exposure on unmanaged BYODs *Lost or stolen BYODs that contain sensitive data, with less than 1 in 4 can be remotely wiped. * When BYODs bypass inbound filters normally applied to corporate devices, they’re vulnerable to malware and the list goes on and on 
TheSoulfulEMU's curator insight,
September 24, 2013 10:12 AM
Now that you know it, so DONT- BYOD!!! Got it?
With the threat already in ads, are mobile users left vulnerable to attacks?
Though developers need to be very careful installing ad networks in their apps, users can still protect themselves by
===> making sure that the Android system setting ‘Unknown sources’ is unchecked to prevent dropped or drive-by-download app installs and installing security apps like Lookout to as their first line of defense against malware. <===
Gust MEES's insight:
===> making sure that the Android system setting ‘Unknown sources’ is unchecked to prevent dropped or drive-by-download app installs and installing security apps like Lookout to as their first line of defense against malware. <===
Learn more:
- http://www.scoop.it/t/apps-for-any-use-mostly-for-education-and-free

Gust MEES's curator insight,
August 16, 2013 8:40 AM
===> making sure that the Android system setting ‘Unknown sources’ is unchecked to prevent dropped or drive-by-download app installs and installing security apps like Lookout to as their first line of defense against malware. <===
Learn more:
- http://www.scoop.it/t/apps-for-any-use-mostly-for-education-and-free
|
This week in the world of Android saw news of a new site for those who want to fix their own gadgets, an easy way to run Android apps under Windows, and an Android trojan is out that works even when you think you're device is shut down. Learn more: - http://www.scoop.it/t/apps-for-any-use-mostly-for-education-and-free/?tag=Android - http://www.scoop.it/t/apps-for-any-use-mostly-for-education-and-free/?tag=Mobile-Security
Gust MEES's insight:
This week in the world of Android saw news of a new site for those who want to fix their own gadgets, an easy way to run Android apps under Windows, and an Android trojan is out that works even when you think you're device is shut down. Learn more: - http://www.scoop.it/t/apps-for-any-use-mostly-for-education-and-free/?tag=Android - http://www.scoop.it/t/apps-for-any-use-mostly-for-education-and-free/?tag=Mobile-Security
Remote wiping? Encryption? Secure passcode? Here are 10 tips to ensure you keep your smartphone just as secure as your PC. 1. Always secure your smartphone with a password 2. Ensure that your device locks itself automatically 3. Install security software 4. Only download apps from approved sources 5. Check your apps' permissions 6. Don't miss operating system updates 7. Be wary of any links you receive via email or text message 8. Encrypt your smartphone 9. Turn off automatic Wi-Fi connection 10. Turn off Bluetooth and NFC when not in use Read full article here: - https://nakedsecurity.sophos.com/2013/10/08/10-tips-for-securing-your-smartphone/ Learn more: - https://gustmees.wordpress.com/2014/11/25/digital-citizenship-social-media-and-privacy/
Gust MEES's insight:
Remote wiping? Encryption? Secure passcode? Here are 10 tips to ensure you keep your smartphone just as secure as your PC. 1. Always secure your smartphone with a password 2. Ensure that your device locks itself automatically 3. Install security software 4. Only download apps from approved sources 5. Check your apps' permissions 6. Don't miss operating system updates 7. Be wary of any links you receive via email or text message 8. Encrypt your smartphone 9. Turn off automatic Wi-Fi connection 10. Turn off Bluetooth and NFC when not in use Read full article here: - https://nakedsecurity.sophos.com/2013/10/08/10-tips-for-securing-your-smartphone/ Learn more: - https://gustmees.wordpress.com/2014/11/25/digital-citizenship-social-media-and-privacy/ 
Elizabeth Milovidov's curator insight,
December 1, 2014 9:24 AM
Is your phone secure? Read these 10 tips for guidance.
A system designed to let carriers remotely install software on phones, or change their settings without a user noticing, is open to abuse.
Gust MEES's insight:
A system designed to let carriers remotely install software on phones, or change their settings without a user noticing, is open to abuse.
During his talk at HOPE/X Jonathan Zdziarski detailed several undocumented services (with names like 'lockdownd,' 'pcapd,' 'mobile.file_relay,' and 'house_arrest') that run in the background on over 600 million iOS devices. Zdziarski's questions for Apple include:
... and his last slide (page 57 of the PDF) sums it up nicely:
Learn more:
Gust MEES's insight:

Gust MEES's curator insight,
July 21, 2014 9:31 AM
During his talk at HOPE/X Jonathan Zdziarski detailed several undocumented services (with names like 'lockdownd,' 'pcapd,' 'mobile.file_relay,' and 'house_arrest') that run in the background on over 600 million iOS devices. Zdziarski's questions for Apple include:
... and his last slide (page 57 of the PDF) sums it up nicely:
Learn more:
The number of bad bots has grown exponentially in recent years, driving poor internet performance for individuals and the loss of control over connected devices; wholesale theft of online intellectual property, content and data; unnecessarily high bandwidth fees; and compromised websites that are otherwise key to mission-critical functions. In fact, bad bots almost doubled as a percentage of all web traffic over the course of 2013, from 12.25% to 23.6%. And the number of mobile bots is up a staggering 1,000%. Learn more: - https://gustmees.wordpress.com/2012/07/07/bring-your-own-device-advantages-dangers-and-risks/ - http://www.scoop.it/t/securite-pc-et-internet/?tag=Botnet - http://www.scoop.it/t/securite-pc-et-internet/?tag=Mobile+Security
A shake-up is coming to the mobile security industry, and it will happen when Google begins to secure its Android environment, David Duncan, CMO of Webroot, says. When you look at most of the mobile apps, you accept the application and its privileges settings, and there is very little ability for you to customise those settings, so you either agree or disagree. App developers are trying to monetise their apps, because remember, most of these are being sold for $1.99 or they're free, so the only way that they are going to make money is collecting and harvesting data, and selling it to a data house, who in turn is going to sell it to advertisers. Learn more: - http://www.scoop.it/t/apps-for-any-use-mostly-for-education-and-free
Gust MEES's insight:
When you look at most of the mobile apps, you accept the application and its privileges settings, and there is very little ability for you to customise those settings, so you either agree or disagree. App developers are trying to monetise their apps, because remember, most of these are being sold for $1.99 or they're free, so the only way that they are going to make money is collecting and harvesting data, and selling it to a data house, who in turn is going to sell it to advertisers. Learn more: - http://www.scoop.it/t/apps-for-any-use-mostly-for-education-and-free
. . WHAT Are Apps? [START Text from Wikipedia] A mobile app, short for mobile application, or just app, is application software designed to run on smartphones, tablet computers and other mobile dev... 
Jacqueline Taylor-Adams's curator insight,
March 27, 2014 11:55 AM
We rescooped this article from our (the Urban Tech Fair's) Czar of Education, Bonnie Bracey Sutton who shared this thought provoking article. What say, ye? ______________________ Be part of the Access, Education, and Commerce movement, the Urban Tech Fair www.UrbanTechFair.org
Here are some resolutions you can easily keep, and you will be glad you did! Our 5-point checklist to help you make essential improvements to your mobile security in 2014.
Gust MEES's insight:
The existence of another “master key” bug that can be used to push malware onto Android users has been publicly disclosed by Jay Freeman (a....
Gust MEES's insight:
There has been a veritable parade of headlines and news stories in even the mainstream consumer press about the increasing security risk presented by smartphones – a.k.a. the small yet powerful computers that most of us carry around in our pockets.
===> Trend Micro recently released data showing that there will be more than one million malware variants in the market by the end of this year. <===
Gust MEES's insight:
===> Trend Micro recently released data showing that there will be more than one million malware variants in the market by the end of this year. <===
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Mobile-Security
- http://gustmees.wordpress.com/2012/07/07/bring-your-own-device-advantages-dangers-and-risks/
- http://www.scoop.it/t/apps-for-any-use-mostly-for-education-and-free
Yesterday's iOS 7 update brought a slew of bug fixes, 80 in total, to Apple devices.
Gust MEES's insight:
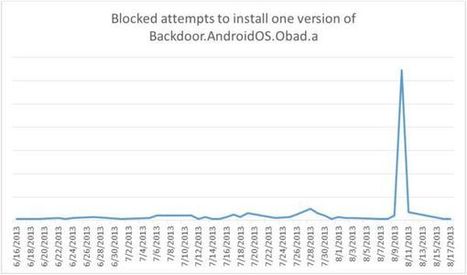
In late May we reported on the details of Backdoor.AndroidOS.Obad.a, the most sophisticated mobile Trojan to date. At the time we had almost no information about how this piece of malware gets onto mobile devices.
Gust MEES's insight:
|






![BYOD Pros and Cons in Education [Infographic] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/Ch1oqxgT1jQ06m3I7BtCdDl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)

![BYOD Security Issues [Infographic] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/CaiNaHRcRGZDVZM2V3tufTl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)














Learn more:
- https://gustmees.wordpress.com/2014/03/05/often-asked-questions-are-there-cyber-security-dangers-with-apps-and-whats-about-privacy/
- https://gustmees.wordpress.com/?s=twitter
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?tag=Botnet
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Botnet